How Email Aliases Help You Detect Phishing Attacks
Malicious emails are getting harder to detect. Bad actors use carefully crafted, authentic looking emails, often containing content gleaned from social media sites or data breaches, to create an air of trustworthiness. The goal of these “social engineering” tactics, which often play to human emotions, is to trick us into revealing sensitive personal information or to take action, such as buying gift cards or wiring funds. As these “phishing attacks” become harder to distinguish from legitimate email, what’s a user to do for help?
Using ManyMe is a good start, as the consistent use of ManyMe email aliases makes it easier to detect and avoid phishing attacks and other fraudulent messages.
While ManyMe takes a number of steps to protect its users from malicious emails, perhaps the most valuable measure is its unique analysis of “To” and “From” email addresses, where the To address is the ManyMe alias (which we refer to as the FlyBy). This analysis guides the content of the Control Strip that is applied at the top of every message forwarded by ManyMe, and the Control Strip makes phishing attacks immediately apparent.
Let’s take a look at two Control Strip examples from malicious messages. The first example, allegedly from Pope Francis, exploits the COVID-19 pandemic by asking the recipient to click on a link to make a donation to the poor.
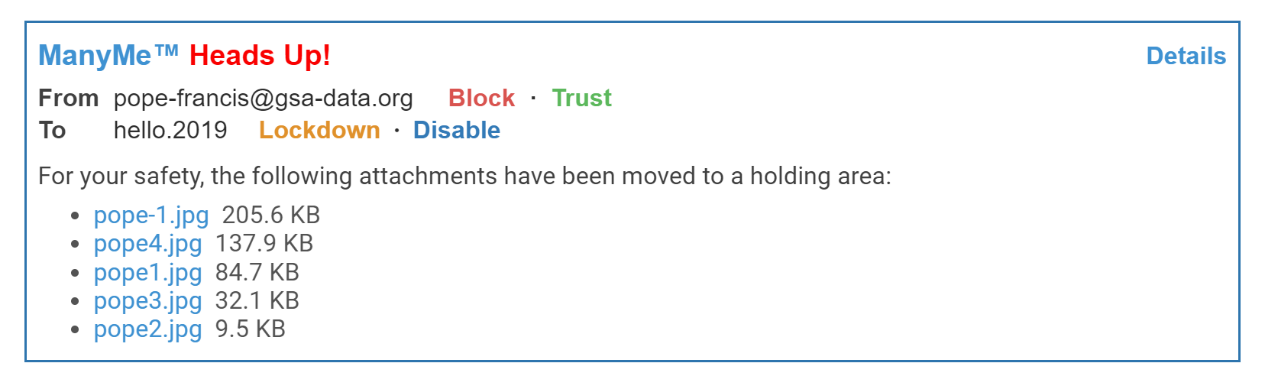
You’ll notice that both the To and From addresses are odd – why would Pope Francis be sending an email from “@gsa-data.org”, and why would the message be sent to the FlyBy “hello.2019?” Recognizing these and other factors, ManyMe tags the message with a “Heads Up!”, advising the user to proceed with caution. Notice also that the message attachments are being hosted in the ManyMe cloud for added safety – if you don’t want them, they’ll never reach your device.
Unfortunately, bad actors routinely falsify the message From address to trick recipients, in what is called a “display name spoofing attack.” To help counter this exploit, when ManyMe’s analysis determines it to be relevant, the Control Strip displays the “Envelope From” address, which is generally not seen by message recipients, but which can provide a clue that a message is suspicious.
The next example of a phishing attack is taken from an email allegedly sent by a tax accountant at a leading public accounting firm.
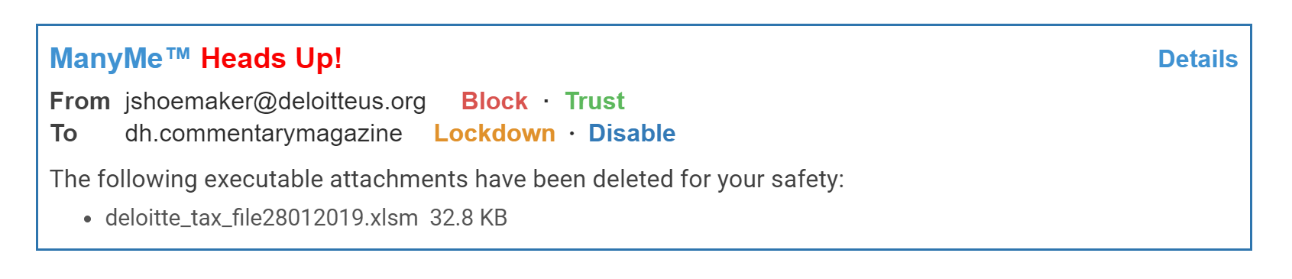
In this case, you can easily see that the message was sent to an alias that had been disclosed to a magazine, not to the accounting firm, and that the message had an attachment that included executable code, which was deleted for safety. Deleting dangerous code is an example of ManyMe’s focus on “effortless security,” which is our quest to incorporate best practices into ManyMe without requiring any user effort. Once again, ManyMe tags the message with a “Heads Up!” to attract added scrutiny to the message.
The more consistently that you use ManyMe aliases, such that more and more of your commercial, impersonal email arrives on different aliases, the broader ManyMe’s protection becomes. Hence our suggestion that you save your personal email address for your family, friends and professional colleagues, and use ManyMe aliases for everything else.
